What the sh*t is going on?
By now you’ve got questions about the timer, or maybe you’re here from LinkedIn.
Allow me to explain some things.
- I developed a series of CTFs that started easy and gradually got more difficult
- The CTFs were meant to help newcomers better understand business concepts and technologies
- Those whom bested the first active CTFs got a shot at being a #destinyCTF Keyholders
This put Azure Cloud login credentials into the hands of the Keyholders.
They were the first generation of students learning Azure security architecture from NSS.
Listed below is the Keyholder’s Agenda, and the hands-on skills they developed together.
-Shane


Azure Security Engineering I
09-14-2020 - 09-21-2020
“Throughout 2020, 95% of cloud security failures are going to be the customer’s fault.”
-Orin Thomas, Microsoft Ignite 2019
Keyholder's Agenda
1. Conditional Access
We will demonstrate and discuss what it takes to start building on the best foot– starting with conditional access and infrastructure-wide multi-factor authentication.
2. Containers, Resources, and Resource Groups
We will then move into what approaches can be used with resource groups, what things are containers and what things aren’t, and how to best leverage IAM with the options you have.
3. Networks, Subnets, and Zero Trust Architecture
We will demonstrate and discuss the nuts and bolts of; and what it takes to build a real enterprise ZTA network the best way– with the future in mind and assumption of breach present in the arch.
4. Storage Accounts, Vaults, and Service and Private Endpoints
We will demonstrate and discuss the best way to build and use Storage Accounts and Keyvaults in Azure, and cover what Service / Private Endpoints are meant for.
5. Policy and Compliance in the Azure cloud
We will demonstrate and discuss how to scope and apply policies to conform infra with PCI, NIST, Azure CIS Benchmark and other relevant security controls.
6. Virtual Machines, limitations with IAM and Azure AD
We will demonstrate and discuss how to build resilient virtual machines that conform to availability and failover / fail-back prerequisites, and how to approach each OS style with the best IAM solution possible for the scenario.
7. Updates, DR, Backups, and Managed Identities
We will demonstrate and discuss backups and DR, as well as the best way to approach the idea of a “service account” eg service principal, and what Automation Accounts and managed identities can do for your infrastructure.
8. Operational Excellence and High Availability
We will go over availability limitations, region fail-back, and the true cost of Azure Firewall, DDoS protection, and doing business in the cloud at the lowest bottom line.
9. Practical Application & Hands-On Sessions
09-17-2020 - 09-21-2020
Students take the wheel; the resource locks are removed and students build resilient Zero Trust Azure Cloud architecture with assumption of breach present, and industry-leading best practices, Disaster Recovery, Policy and Compliance initiatives employed.
Azure Security Engineering II
09-21-2020 - 10-1-2020
Keyholder's Agenda
1. Compliance in the multi-cloud
We will cover CIS and controls mappings, how they translate to other controls and systems, and how to best leverage Sentinel Connectors to get the insights you didn’t know you needed.
2. Building the security program
We go over what it really means to give the stakeholders peace of mind– by applying policy and compliance to match rigorous initiatives towards tomorrow’s requirements that truly drive the mission forward.
3. Building the security team
We talk about building trust, building teams, and what it takes to recruit skilled candidates in a cut-throat industry full of poachers– and posers.
4. Assumption of Transparency
We talk about the Assumption of Transparency regarding apps; app developers; over-reaching permissions and the consequences of app sprawl on a connected device.
5. Assumption of Security
We discuss the lack of proper security in today’s production cloud workloads, building on the right foot, and what led Microsoft to quote a number like 95% in 2020.
6. Assumption of Breach
We discuss risk, risk factors, insider threats, and what it really means to build with Assumption of Breach present in the architecture and why it matters.
7. Building with AOB in mind
We go over the practical application of Zero-Trust architecture built with assumption of breach present, and review how the NSS architecture created by the students covers these critical areas.
8. Azure Security Center
We take a high-level overview or “birdseye” of Azure Security Center and discuss how it can be best used to address the company’s security posture.
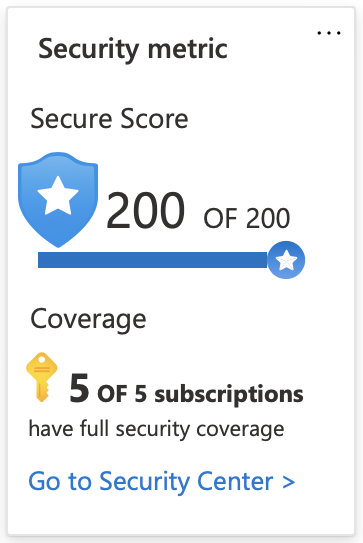
9. Secure Score Index
We look at the Azure Security Score, review what the shield colors mean, what exactly the index is, and how to understand what you’re looking at.
10. Advisor Recommendations
We take a deep dive into how definitions and initiatives can be leveraged to create projects and milestones that use agile sprint methodology to spearhead compliance.
11. Azure Defender
We take a fresh look at the new Azure Defender and how it can be leveraged to provide a killer compliance dashboard for your multi-cloud workloads.
Real arch made by the Keyholders
Build it like you mean breach.